trumpthatbitch
Well-Known Member
- Jun 23, 2017
- 1,299
- 2,113
- 515
You can also further harden your PC with group policy editor (MMC-run as admin) :
Computer Configuration\Policies\Administrative Templates\Windows Components\Microsoft Defender
Antivirus\Exclusions
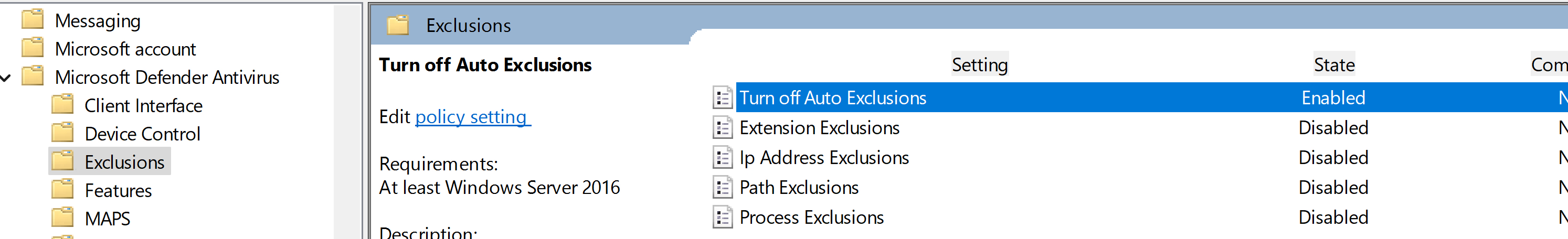
Computer Configuration\Policies\Administrative Templates\Windows Components\Microsoft Defender
Antivirus
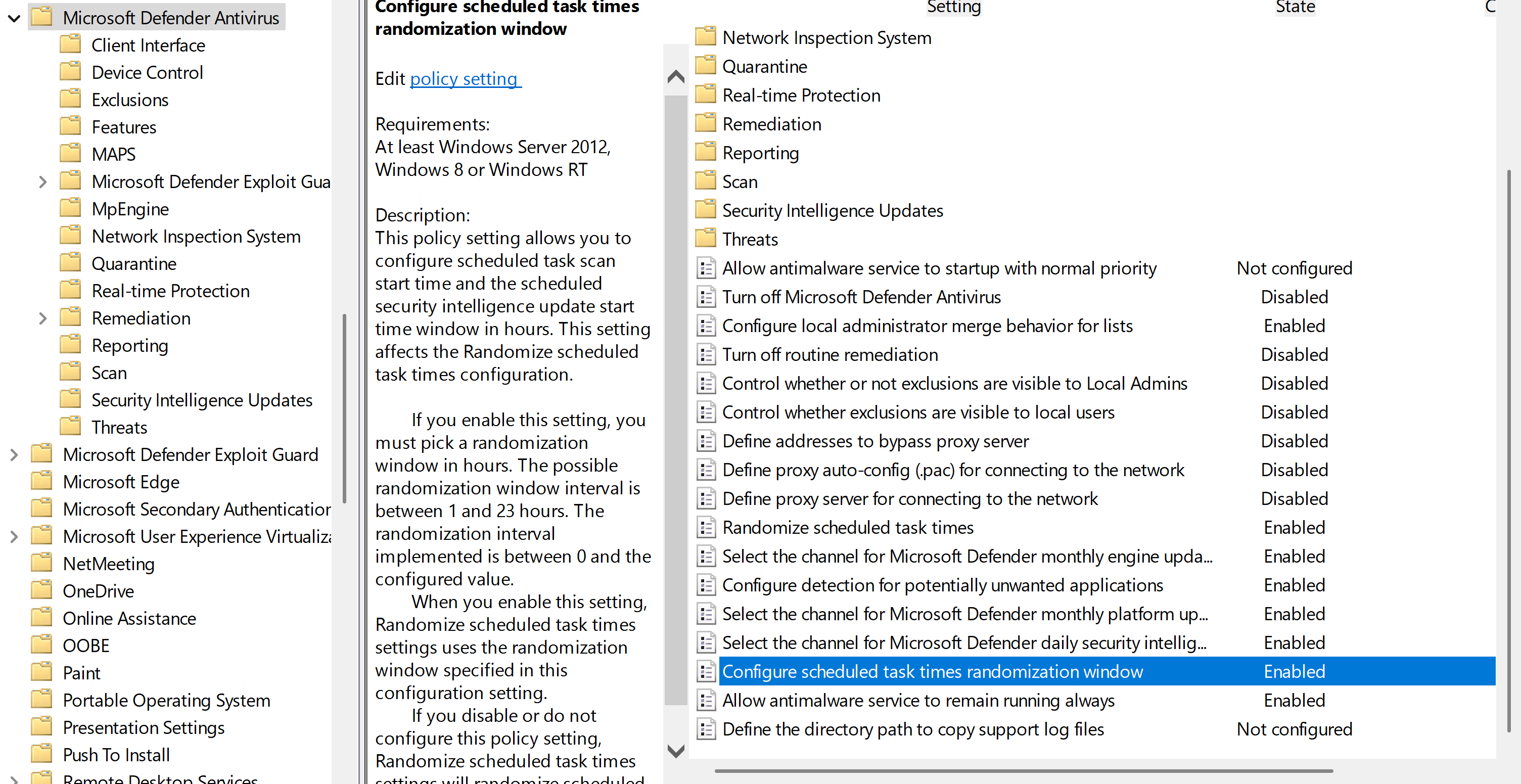
Preview Channel will allow you to receive the latest threat infromation.
Potentially unwanted application maybe you want off it could affect other pirated games or software would suggest turning on then off if you find annoying at least set to audit mode for tracking
Computer Configuration\Policies\Administrative Templates\Windows Components\Microsoft Defender
Antivirus\MpEngine
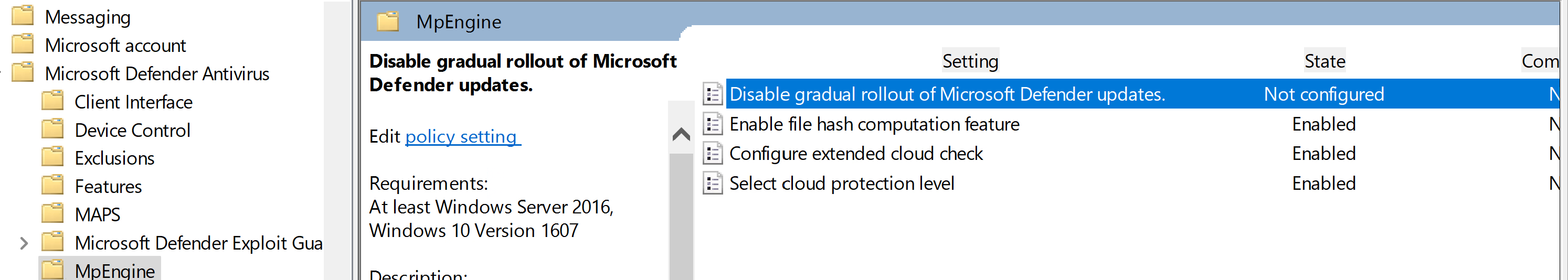
Specify the extended cloud check time in seconds: 50
Select cloud blocking level: High blocking level
or
Select cloud blocking level: High+ blocking level
Computer Configuration\Policies\Administrative Templates\Windows Components\Microsoft Defender
Antivirus\MAPS
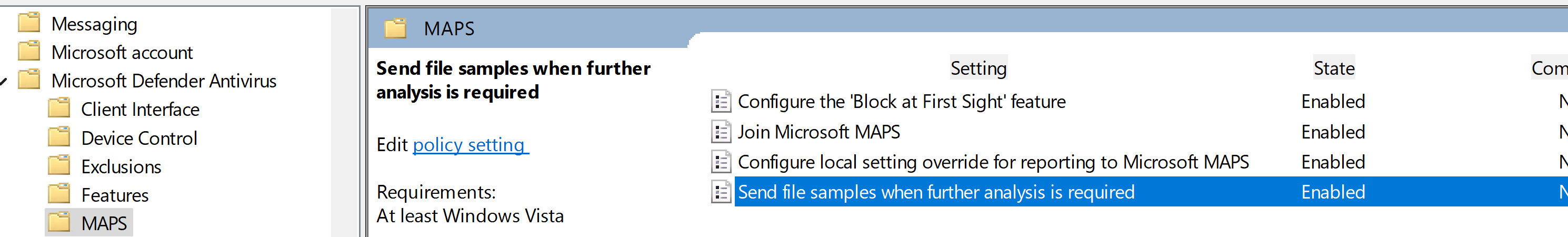
Sent send safe samples automatically
Computer Configuration\Policies\Administrative Templates\Windows Components\Microsoft Defender
Antivirus\Quarantine
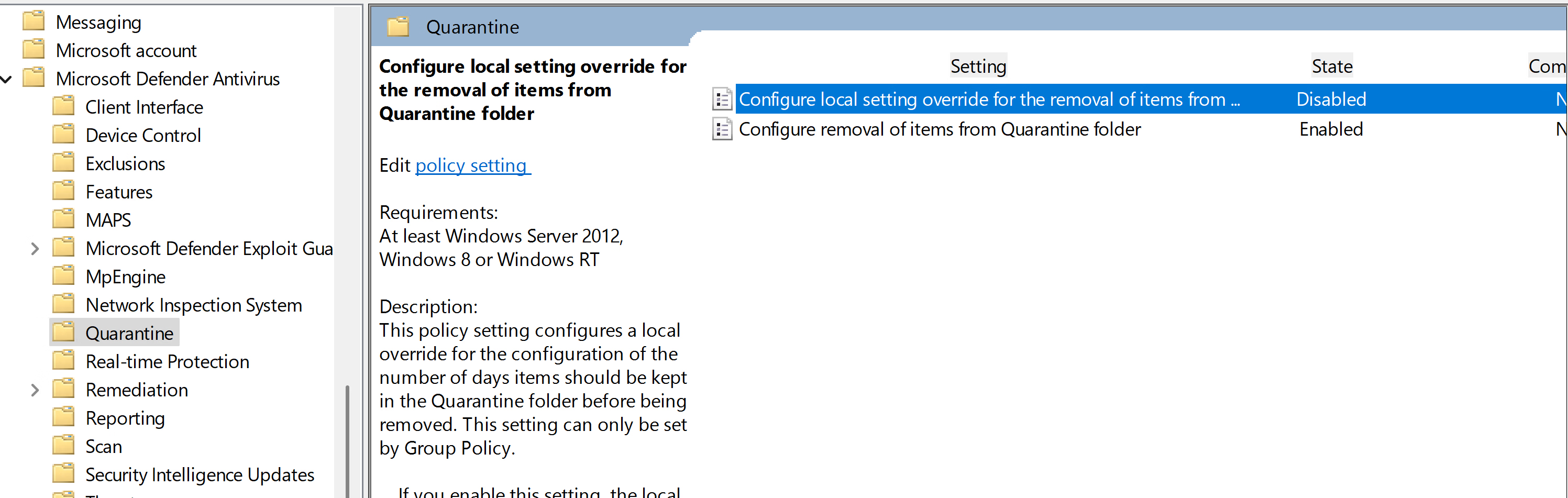
Set to 5days for auditing purposes
Computer Configuration\Policies\Administrative Templates\Windows Components\Microsoft Defender
Antivirus\Real-time Protection
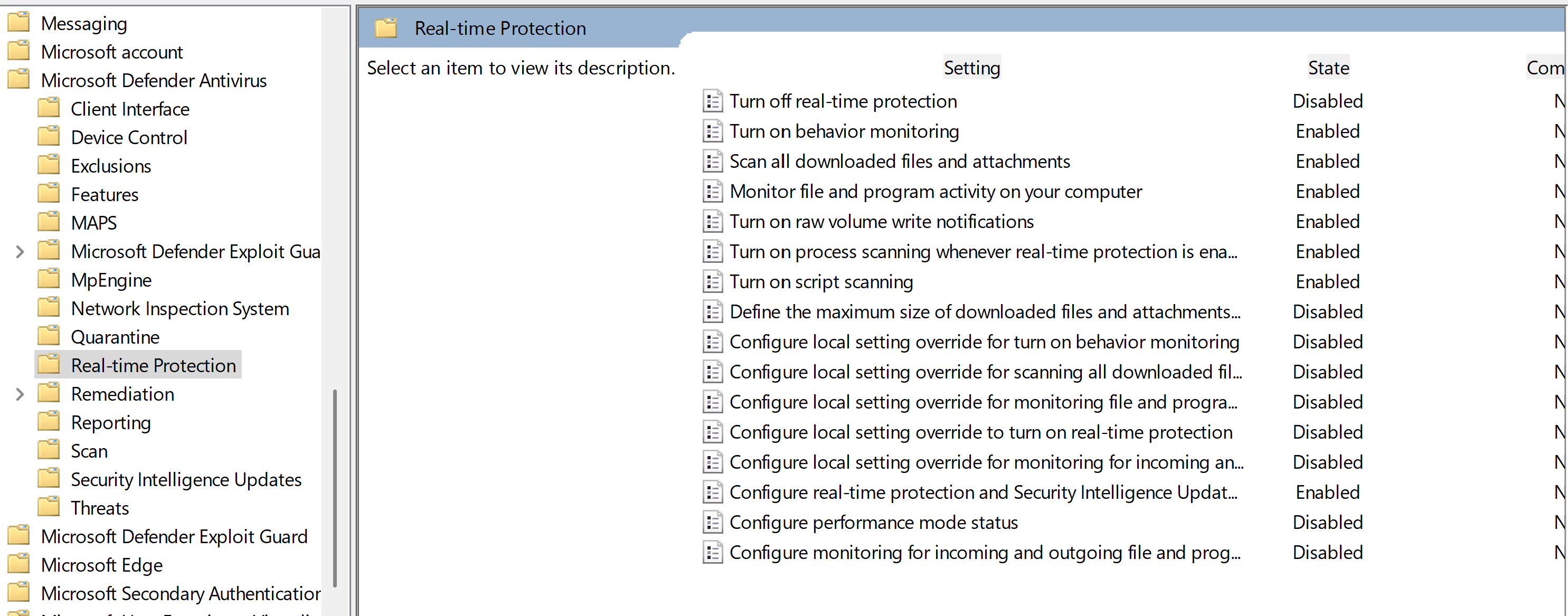
Computer Configuration\Policies\Administrative Templates\Windows Components\Microsoft Defender
Antivirus\Scan
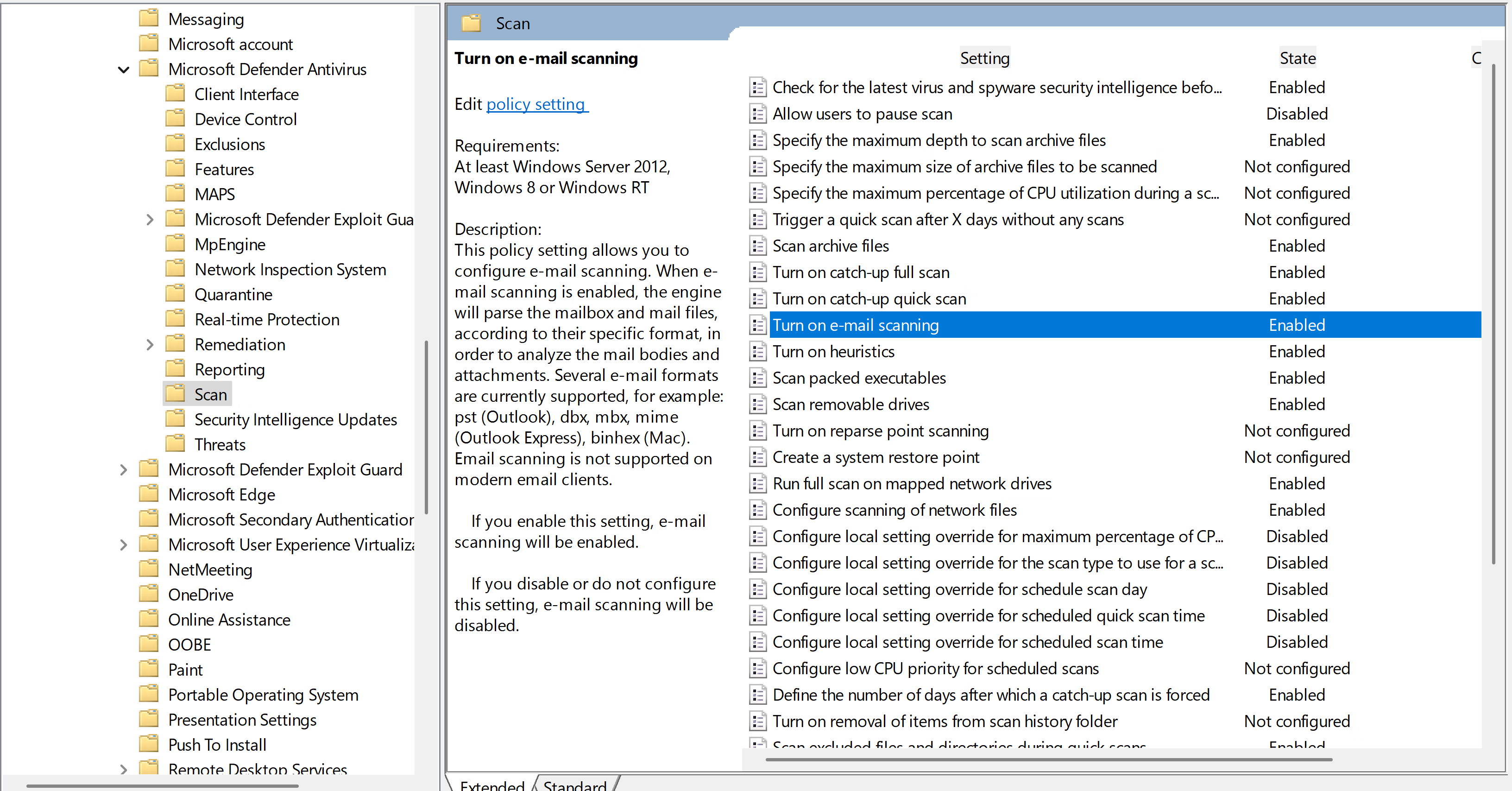
Computer Configuration\Policies\Administrative Templates\Windows Components\Windows PowerShell
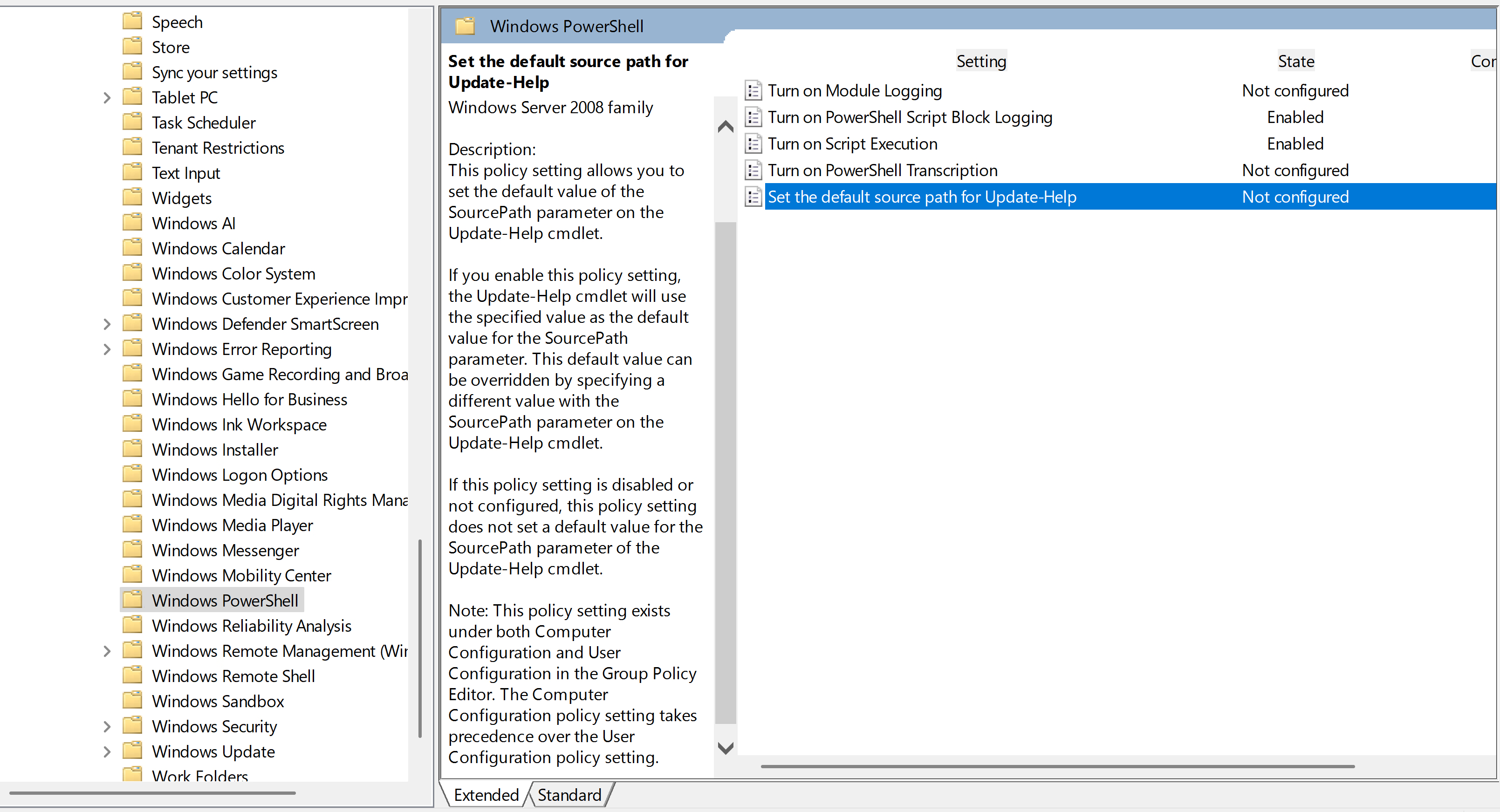
Execution Policy: Allow only signed scripts
-------------------------------------------------------------------------------------------------------------------------------------------------------------------------
To make changes to group policy on Windows Home you need to enable group policy via a workaround:
- Search for MMC, run as admin and then press Enter. You can also run MMC by using CMD-Run as admin-MMC and then enter
- On the File menu, click Add/Remove Snap-in.
- In the Add or Remove Snap-ins dialog box, click Local Group Policy Editor, and then click Add.
- In the Select Group Policy Object dialog box, click ok..
Computer Configuration\Policies\Administrative Templates\Windows Components\Microsoft Defender
Antivirus\Exclusions

Computer Configuration\Policies\Administrative Templates\Windows Components\Microsoft Defender
Antivirus

Preview Channel will allow you to receive the latest threat infromation.
Potentially unwanted application maybe you want off it could affect other pirated games or software would suggest turning on then off if you find annoying at least set to audit mode for tracking
Computer Configuration\Policies\Administrative Templates\Windows Components\Microsoft Defender
Antivirus\MpEngine

Specify the extended cloud check time in seconds: 50
Select cloud blocking level: High blocking level
or
Select cloud blocking level: High+ blocking level
Computer Configuration\Policies\Administrative Templates\Windows Components\Microsoft Defender
Antivirus\MAPS

Sent send safe samples automatically
Computer Configuration\Policies\Administrative Templates\Windows Components\Microsoft Defender
Antivirus\Quarantine

Set to 5days for auditing purposes
Computer Configuration\Policies\Administrative Templates\Windows Components\Microsoft Defender
Antivirus\Real-time Protection

Computer Configuration\Policies\Administrative Templates\Windows Components\Microsoft Defender
Antivirus\Scan

Computer Configuration\Policies\Administrative Templates\Windows Components\Windows PowerShell

Execution Policy: Allow only signed scripts
-------------------------------------------------------------------------------------------------------------------------------------------------------------------------
To make changes to group policy on Windows Home you need to enable group policy via a workaround:
You must be registered to see the links
Last edited: