The VN Connoisseur
Member
- Oct 8, 2017
- 128
- 115
- 170
Hi,
I am trying to edit the main executable of one of the ESCUDE games, since the game saves its configuration to the Documents folder, and I wanna avoid that and make it save in the root folder of the main executable.
Thus far, I have managed to find and interpret the function (mind you, I am dealing with x86 assembly) where is trying to read the original configuration.cfg (it uses a standard Windows API for initialization files) and then it creates a folder in Documents folder called ESCUDE, and then another folder called HimeYuki (both are variables stored in the configuration.cfg).
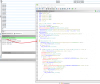
Original code:
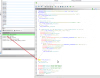
This is the modified snippet:
My idea was to create this function:
and thus far I have this:
Do you have any recommendations on how to approach this? I can pass the entire Ghidra project if needed.
I am trying to edit the main executable of one of the ESCUDE games, since the game saves its configuration to the Documents folder, and I wanna avoid that and make it save in the root folder of the main executable.
Thus far, I have managed to find and interpret the function (mind you, I am dealing with x86 assembly) where is trying to read the original configuration.cfg (it uses a standard Windows API for initialization files) and then it creates a folder in Documents folder called ESCUDE, and then another folder called HimeYuki (both are variables stored in the configuration.cfg).
Original code:
C:
void FUN_004ef860(undefined4 param_1,undefined4 param_2,undefined4 param_3,undefined4 param_4)
{
int createConfigFile;
BOOL BVar1;
uchar *puVar2;
DWORD DVar3;
HWND gameWindow;
HRESULT HVar4;
char *lpString2;
char acStack_428 [4];
tagMSG tStack_424;
CHAR configPath [260];
char acStack_304 [256];
char acStack_204 [256];
char acStack_104 [256];
uint local_4;
local_4 = DAT_0058c730 ^ (uint)acStack_428;
DAT_00c31b24 = param_1;
_setlocale(0,"Japanese_Japan.932");
GetModuleFileNameA((HMODULE)0x0,&iniFile,0x104);
__splitpath(&iniFile,acStack_428,acStack_304,acStack_204,acStack_104);
__makepath(&iniFile,acStack_428,acStack_304,(char *)0x0,(char *)0x0);
FUN_004eded0();
__makepath_s(&DAT_00c31a20,0x104,acStack_428,acStack_304,acStack_204,".cfg");
createConfigFile = findExistingConfigFile(&DAT_00c31a20);
if (createConfigFile != 0) {
FUN_004edfa0(&DAT_00c31a20);
}
if (inheritance != 0) {
__makepath_s(&DAT_00c31a20,0x104,acStack_428,acStack_304,"configure",".cfg");
createConfigFile = findExistingConfigFile(&DAT_00c31a20);
if (createConfigFile != 0) {
FUN_004edfa0(&DAT_00c31a20);
}
if ((((inheritance != 0) && (companyString != '\0')) && (productString != '\0')) &&
(createConfigFile = checkExistsConfigFile(0,5,configPath), createConfigFile != 0)) {
lstrcatA(configPath,"\\");
lstrcatA(configPath,&companyString);
createConfigFile = findExistingConfigFile(configPath);
if ((createConfigFile != 0) ||
(BVar1 = CreateDirectoryA(configPath,(LPSECURITY_ATTRIBUTES)0x0), BVar1 != 0)) {
lstrcatA(configPath,"\\");
lstrcatA(configPath,&productString);
createConfigFile = findExistingConfigFile(configPath);
if ((createConfigFile != 0) ||
(BVar1 = CreateDirectoryA(configPath,(LPSECURITY_ATTRIBUTES)0x0), BVar1 != 0)) {
lstrcatA(configPath,"\\configure.cfg");
lstrcpyA(&DAT_00c31a20,configPath);
createConfigFile = findExistingConfigFile(configPath);
if (createConfigFile != 0) {
FUN_004edfa0(&DAT_00c31a20);
}
}
}
}
}
C:
if ((((inheritance != 0) && (companyString != '\0')) && (productString != '\0')) &&
(createConfigFile = checkExistsConfigFile(0,5,configPath), createConfigFile != 0)) {
getCorrectConfigPath(configPath); --> For now I am trying to recreate this function
createConfigFile = findExistingConfigFile(configPath);
C:
void getCorrectConfigPath(char *configPath)
{
char executablePath[MAX_PATH]; // Buffer to store the path of the executable
char rootFolder[MAX_PATH]; // Buffer to store the root folder (directory)
// Clear the configPath (set it to an empty string)
memset(configPath, 0, MAX_PATH);
// Get the full path of the executable
GetModuleFileNameA(NULL, executablePath, MAX_PATH);
// Extract the root directory from the executable path
__splitpath(executablePath, rootFolder, NULL, NULL, NULL);
// Set the configPath to the root folder
strcpy(configPath, rootFolder);
}
C:
/* WARNING: Unknown calling convention -- yet parameter storage is locked */
void getCorrectConfigPath(char *configPath)
{
char rootFolder [260];
_memset(configPath,0,260);
GetModuleFileNameA((HMODULE)0x0,&stack0xfffffdf4,0x104);
__splitpath(&stack0xfffffdf4,rootFolder,(char *)0x0,(char *)0x0,(char *)0x0);
lstrcpyA(configPath,rootFolder);
return;
}
Last edited: