EDITED: Unsafe or sketchy connections from the binary
I dont want to rise alerts but i do want to express my concerns.
I am not a Blue Team or cybersecurity professional, however after a preliminary investigation, these are the findings regarding this game after the last update:
The game's executable binary (including the original file downloaded directly from Itch.io) triggers a high-severity warning when analyzed with VirusTotal (My standard procedure before executing any game).

A deeper inspection of the binary suggests the presence of
You must be registered to see the links
–like behavior, which is highly unusual for a legitimate video game,
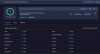
specially for a single player game. The executable performs multiple DNS resolutions that result in connections to frequently changing IP addresses.
Notably, several of these IP addresses initially resolve to servers located in the
United States, but in some cases subsequently
redirect to IP ranges geolocated in India. This pattern is commonly associated with command-and-control (C2) infrastructure and evasive network techniques used by malware.
Fast Flux techniques are typically employed to increase resilience and avoid takedown of malicious infrastructure. Their presence in a standalone game executable, which does not appear to require such networking complexity, raises concerns for me.
Based on these observations, the behavior exhibited by the binary does not align with what would normally be expected from a legitimate game and warrants further investigation.
As I told im not a cybersecurity professional but i think this looks sketchy at least.
- Can someone expand about this topic?
- Am I concerned for nothing?
Best regards!
### IMPORTANT: EDITED ###
After investigating the RPGM engine functionality and the Reverse Engineering of the Binary file, even though it still looks sketchy, it no longer rises heavy suspicions to me. I will still execute it using Sandboxie with network Disabled, no access to Files and admin access blocked just in case.