I don't know why but I never get tired of Elf x Goblin
- Thread starter Bob69
- Start date
3.20 star(s)
13 Votes
Crow Armbrust
Message Maven
- Apr 29, 2018
- 15,879
- 5,661
- 832
NotSomeone
Member
- Nov 29, 2017
- 209
- 391
- 227
game is kinda shit
anyway, I downloaded the full save from doujin-savedata, here it is if anyone wants it
anyway, I downloaded the full save from doujin-savedata, here it is if anyone wants it
sunsamuel252
Member
- Nov 21, 2019
- 162
- 149
- 121
ps3king1336
Member
- Mar 25, 2017
- 279
- 263
- 289
I-Love-Adventure
Engaged Member
- Feb 16, 2019
- 3,642
- 1,446
- 348
RepZwasHere
Newbie
- Dec 29, 2021
- 75
- 30
- 163
Why is this not tagged as AI? Low effort AI slop.
- Dec 30, 2020
- 9,306
- 4,294
- 436
SerenaOfTheCorruptedMines-1.0
rpdl torrents are unaffiliated with F95Zone and the game developer.
Please note that we do not provide support for games.
For torrent-related issues use here, or join us on
You don't have permission to view the spoiler content.
Log in or register now.
Please note that we do not provide support for games.
For torrent-related issues use here, or join us on
You must be registered to see the links
!
You must be registered to see the links
,
You must be registered to see the links
. Downloading issues? Look here.Khalic
Newbie
- Feb 6, 2023
- 49
- 34
- 28
I checked just in case in a virtual machine to see if the archive was good to run and well through Hybrid Analysis in a controlled sandbox environment, and the results indicate it as a high-risk malicious file.
The dynamic analysis showed typical malware behaviors:
Even if in virus total it looks like a false positive because zillya is not the greatest one
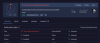
The results of hybrid analysis
I do not recommend to run this file on your main PC. Even if antivirus doesn’t flag it, its behavior indicates it’s malicious. Investigate only in a sandbox or virtual machine.
Because based on the Hybrid Analysis report, the file could:
Also I used the file in GoFile link pinned in the OP to run the tests
The dynamic analysis showed typical malware behaviors:
- Virtual environment evasion – tries to avoid detection in virtual machines.
- Registry modifications – can alter Windows registry keys, which is commonly used for persistence.
- Process creation/modification – may attempt to establish persistent or elevated processes.
- DLL injection – injects code into legitimate processes, making detection harder.
Techniques detected (MITRE ATT&CK)
The sandbox mapped 253 indicators to 134 techniques and 12 tactics, including:- T1592.003 – Firmware information gathering
- T1106 – Native API execution
- T1559 – Inter-process communication
- T1059.003 – Windows command shell usage
- T1569.002 – Service execution
- T1129 – Shared modules
- These are commonly associated with advanced malware, trojans, and remote access tools.
Even if in virus total it looks like a false positive because zillya is not the greatest one
You must be registered to see the links

The results of hybrid analysis
You must be registered to see the links

I do not recommend to run this file on your main PC. Even if antivirus doesn’t flag it, its behavior indicates it’s malicious. Investigate only in a sandbox or virtual machine.
Because based on the Hybrid Analysis report, the file could:
- Establish persistence
- Modify Windows registry keys or create services so it runs automatically after reboot.
- Execute code in other processes
- Uses DLL injection to hide inside legitimate Windows processes.
- Run malicious commands
- Executes commands through Windows shell to manipulate the system.
- Communicate over the network
- Potentially connects to external servers (could download more malware or send data).
- Other advanced malware actions
- Gather system or firmware information, potentially open backdoors, or install additional malicious modules.
Also I used the file in GoFile link pinned in the OP to run the tests
Last edited:
D.K
Member
- Nov 3, 2017
- 139
- 296
- 287
The only reason it's tagged in both Hybrid and VirusTotal is because of Zillya. Unless another AV some how picks it up as a virus (news flash, you could've just looked up the trojan itself and actually found a thread from 2 years ago talking about the very trojan), it's almost guaranteed a false positive.I checked just in case in a virtual machine to see if the archive was good to run and well through Hybrid Analysis in a controlled sandbox environment, and the results indicate it as a high-risk malicious file.
The dynamic analysis showed typical malware behaviors:
- Virtual environment evasion – tries to avoid detection in virtual machines.
- Registry modifications – can alter Windows registry keys, which is commonly used for persistence.
- Process creation/modification – may attempt to establish persistent or elevated processes.
- DLL injection – injects code into legitimate processes, making detection harder.
Techniques detected (MITRE ATT&CK)
The sandbox mapped 253 indicators to 134 techniques and 12 tactics, including:
- T1592.003 – Firmware information gathering
- T1106 – Native API execution
- T1559 – Inter-process communication
- T1059.003 – Windows command shell usage
- T1569.002 – Service execution
- T1129 – Shared modules
- These are commonly associated with advanced malware, trojans, and remote access tools.
Even if in virus total it looks like a false positive because zillya is not the greatest one
You must be registered to see the links
View attachment 5219745
The results of hybrid analysis
You must be registered to see the links
View attachment 5219776
I do not recommend to run this file on your main PC. Even if antivirus doesn’t flag it, its behavior indicates it’s malicious. Investigate only in a sandbox or virtual machine.
Because based on the Hybrid Analysis report, the file could:
While I have tried to interpret the data accurately, I cannot guarantee that it is 100% correct, im not a malware expert so i hope that somebody double check what i just said o7
- Establish persistence
- Modify Windows registry keys or create services so it runs automatically after reboot.
- Execute code in other processes
- Uses DLL injection to hide inside legitimate Windows processes.
- Run malicious commands
- Executes commands through Windows shell to manipulate the system.
- Communicate over the network
- Potentially connects to external servers (could download more malware or send data).
- Other advanced malware actions
- Gather system or firmware information, potentially open backdoors, or install additional malicious modules.
Also I used the file in GoFile link pinned in the OP to run the tests
Merlin2013
Member
- Jul 4, 2017
- 397
- 222
- 236
Khalic
Newbie
- Feb 6, 2023
- 49
- 34
- 28
Tbh I mostly didn’t trust the file because of the hybrid sandbox results that detected a suspicious behavior. Because like you said in the AV is just Zillya who detected it in both cases, but what concerns me a bit is the analysis that im assuming is more reliable than a single static AV detection.The only reason it's tagged in both Hybrid and VirusTotal is because of Zillya. Unless another AV some how picks it up as a virus (news flash, you could've just looked up the trojan itself and actually found a thread from 2 years ago talking about the very trojan), it's almost guaranteed a false positive.
petweiss
Newbie
- Jun 24, 2022
- 38
- 118
- 147
I was disappointed with the game. Apparently you only get the good ending if you don’t corrupt the heroine in a certain amount, but when you go to farm EXP, you end up being forced to face monsters that have a high chance of corrupting you. It is difficult to play like this.
Arenadelson1
Newbie
- May 16, 2024
- 38
- 64
- 94
Lmao what an anticlimatic ending. Win random boss fight against some mid rank goon, get your throat slit anyway and die. Not even the devs wanted to continue with this trash.
lusciousboy01
Member
- Nov 15, 2017
- 160
- 396
- 268
What? No, no, no.I was disappointed with the game. Apparently you only get the good ending if you don’t corrupt the heroine in a certain amount, but when you go to farm EXP, you end up being forced to face monsters that have a high chance of corrupting you. It is difficult to play like this.
There is only one thing that determines the ending path.
To get the good ending, you need to receive the "Signal Orb" from the female engineer and you need to have it equipped during the final confrontation.
If you have the "Signal Orb", miners rescue Serena after she's defeated.
If you don't have it, Serena gets her throat slit and die in the darkness.
