While I don't intend to defend anything here, understand that the term "Trojan", when it comes to viruses, was picked for a reason. It literally means "to infiltrate stealthily". Unfortunately, it's the same pattern used by auto translation programs as well who piggyback on the .exe file and inject translation layer turning JP text to EN in real time.
The gentleman above me seems to not understand that virus scanners have no way to know that. They don't "play" what you feed them to ascertain what the purpose of the exe is. They just read symptoms.
- Is the .exe untouched? Nope. => Reality: Modified to run in tandem with translation software
- Is their another command affecting the exe being scanned? Yep. => Reality: Telling the game to run the text for translation before displaying.
- Is this command sending data to another web source? Yep. => Reality: Pinging GoogleTranslate/DeepL for translation requests.
- Are we sure it's a virus? Nope, but it's suspicious behavior. => Reality: I can't be sure because I can't see. But, if it quacks like a duck, and I hear wings fluttering, it's most likely a duck, so might as well say it's a virus just to be on the safe side.
There is a reason "false positives" exist even within top tier AV suites. Heck they flag anything as virus if it doesn't have a digital signature, something small devs have a headache dealing with as they don't have the time or money to do that just to help others run scripts for a small task.
Rest of-course is your call. It's your computer. Do what you want.
But if someone actually wants to learn how to look for signs of true or false positives, while not 100% guaranteed way, you can figure out some clues. For example, take this AV scan 2 posts above me:
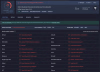
- First thing, the gentleman ran the entire package through the scanner. EVEN IF the game had legitimate virus, we have no idea what section had the virus. For all we know, all of it is a virus, or just one file is.
- Second, look at Popular Threat Label: trojan.cheating.engine/inject2. You really don't need to be a data scientist to figure out what that means. Anyone with a basic English comprehension can figure out that the most likely ping by the scanners are that of a cheat engine that is injecting code into the game. Cheating Engine =/= Virus. At least not most of the time. There are better, more easier ways, to telemetry a wormware into a system.
- Speaking of scanners, isn't it odd that only 22 out of 63- less than half of the scanners, ACTUALLY pinged a hit? That's odd, no? Considering how AV databases are globally shared, it makes little sense for something as old as 2019, has a virus that still hasn't been added on the collective threat base?
- Finally, look at the so called "Anti Virus Scanners". Just look at their names. While I haven't used a dedicated anti virus in years(Linux user here who doesn't put my digital dick in random websites and software), it's very odd that I can't view most of the tried and tested giants of the AV world on the red list. The only ones I'm familiar with are ESET, Microsoft, Symantec and for some absurd reason Google? Since when they did start fielding consumer level AVs?
Even if I put aside the known names, are you really going to trust random AV results just because they displayed something in red? Honestly, if you do, you really need to read up on AV trust index thesis. There is a reason not all AVs are considered equal.
Either way, rest is upto you as the user. Use your own brain to find the right answer or just trust some tool to make the call for you.